Business Logic Flaw in EMSigner’s Web Application User Management Allows Unauthorized Modification of User Names and Privileges
Summary
Name: Business Logic Flaw in EMSigner’s Web Application User Management Allows Unauthorized Modification of User Names and Privileges
Product: EMSigner
Affected versions: EMSigner version 2.8.7
Affected Component: EndPoint /eMsecure/Users/AdhocUser and web parameter “Name” Attack Type: Remote
Vulnerability Type: Incorrect Access Control
Impact: Integrity
CVSSv3.1 Vector: AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:L
CVSSv3.1 Base Score: 7.1
CVE ID(s): CVE-2023-43901
Description
Incorrect access control in the AdHoc User creation form of EMSigner v2.8.7 allows unauthenticated attackers to arbitrarily modify usernames and privileges by using the email address of a registered user.
Vulnerability
The “Business Logic Flaw in EMSigner’s Web Application User Management Allows Unauthorized Modification of User Names and Privileges” vulnerability is rooted in a critical business logic flaw within the user management system of the EMSigner web application. This flaw permits unauthorized users to manipulate user data, including changing user names and downgrading user privileges, when using the email address of a registered user.
Attack Vectors
The vulnerability is exploited through the web application’s AdHoc User creation form or web request. An attacker can gain unauthorized access to the form or request, allowing them to modify user names and privileges by using the email address of a registered user. This business logic flaw permits unauthorized alteration of existing user data, potentially leading to unauthorized actions and privilege downgrading.
Explotation
During the web application assessment for one of our clients, we performed an assessment on a web app that used the emSigner software. Now, speaking of emSigner, this software is a document automation solution that helps organizations completely eliminate paper from all workflows and create an end-to-end document automation ecosystem, digitizing documents using legally valid digital signatures.
While researching this web app, we discovered a vulnerability that allows unauthorized modification of user names and downgrading of user privileges by exploiting the AdHoc User creation form or web request. The vulnerability allows overwriting or modifying existing user data, including user names and privileges, when using the email address of a registered user.
Below, we will explain this vulnerability and the steps needed to exploit it.
First logged in as a low-privilege user [email protected] and clicking on the option to create Adhoc Users as shown in figure 1
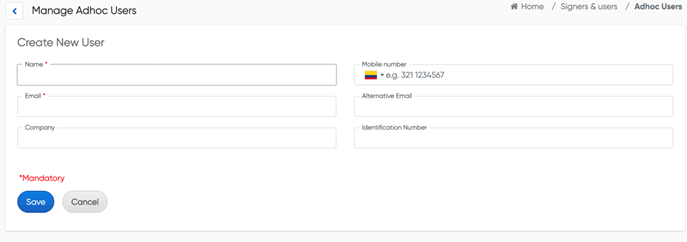
Figure 1 Adhoc Users
An attacker sends an HTTP POST request to the AdHoc User creation endpoint at https://domain.com/eMsecure/Users/AdhocUser with the “Name” parameter set to a new name (e.g., “Juan”) and the email address of an existing user as shown in figure 2.
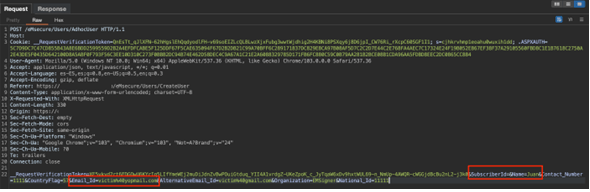
Figure 2 Request HTTP
The server processes the request and successfully updates the user’s name and downgrades their privileges associated with the provided email address as shown in figure 3.
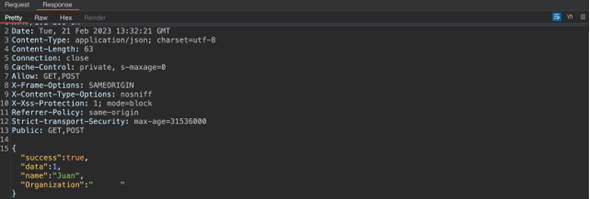
Figure 3 Response HTTP
The victim’s user name is now changed, and they are left with the minimum privileges in the application as shown in figure 4.
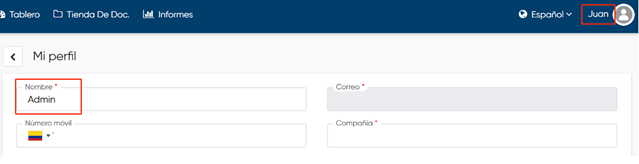
Remediation
An updated version of EMSigner is available at the vendor page.
Credits
The vulnerability was discovered by Jean Paul Granados from SecPro’s Company (https://secpro.co/ – https://secpro.llc/).
References
Vendor page https://www.emsigner.com/
Timeline
2023-02-27
Vulnerability discovered.
2023-05-08
Vendor contacted.
2023-05-24
Vendor replied acknowledging the report.
2023-09-01
Vulnerability patched.
2023-10-27
Public Disclosure.
Contact Us
+1 (804) 256-8316
2034 Eisenhower Ave # 170 Alexandria, VA 22314
Monday-Friday: 9am - 5pm


