Privilege Escalation via “Forgot your password” functionality
Summary
Name: Privilege Escalation via “Forgot your password” functionality
Product: EMSigner
Affected versions: EMSigner version 2.8.7
Affected Component: Forgot your password function. EndPoint /Areas/Login/PasswordRecovery and Web Parameter “Email”
Attack Type: Remote
Impact: Escalation of Privileges
CVSSv3.1 Vector: AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
CVSSv3.1 Base Score: 8.8
CVE ID(s): CVE-2023-43902
Description
Incorrect access control in the Forgot Your Password function of EMSigner v2.8.7 allows unauthenticated attackers to access accounts of all registered users, including those with administrator privileges via a crafted password reset token.
Vulnerability
The “Privilege Escalation via ‘Forgot your Password’ functionality” vulnerability arises due to insufficient access controls within the password reset process of the application. Specifically, the application exposes an activity related to password reset and fails to adequately validate and enforce access privileges, allowing low-privileged users to manipulate certain parameters to gain unauthorized access and potentially reset the passwords of accounts with higher privileges, including administrator accounts.
Attack Vectors
The vulnerability can be exploited through an “Authentication Bypass” attack vector. To exploit this vulnerability, an attacker with low-privileged access can manipulate certain parameters in the password reset token generated by the “Forgot your password” functionality. By crafting a malicious password reset token, the attacker can establish a new password for accounts with administrator privileges. This leads to unauthorized access to higher-privileged accounts and potential exposure of sensitive information.
Explotation
During the web application assessment for one of our clients, we performed an assessment on a web app that used the emSigner software. Now, speaking of emSigner, this software is a document automation solution that helps organizations completely eliminate paper from all workflows and create an end-to-end document automation ecosystem, digitizing documents using legally valid digital signatures.
While researching this web app, we discovered a vulnerability that allows an attacker to gain access to the accounts of all registered users on the web portal, including those with higher privileges. By exploiting the “Forgot your password” functionality, a low-privileged user can modify certain parameters in the reset token to establish a new password for accounts with administrator privileges. This can potentially lead to unauthorized access, disclosure of sensitive information, and disruption of the affected system.
Below, we will explain this vulnerability and the steps needed to exploit it.
An attacker with a low privileged account within the web portal navigates to the affected url “forgot your password” as shown in figure 1 and triggers the process to reset his password with the testing account je**.***.********@gmail.com
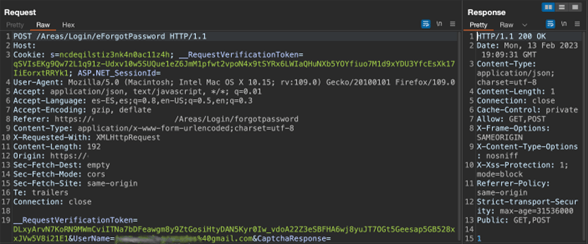
Figure 1 Request forgot Password
After filling out the form and completing the process, the attacker receives a password reset linking the email je**.***.********@gmail.com, which allows them to set a new password for your account as shown in figure 2 :

Figure 2 Password Reset Link
The consultants clicked on the link and observed that it triggered the PasswordRecovery form, as depicted in Figure 3. Here it was possible to modify the email parameter and set a new password for a different account. However, in order to do so, the consultants had to first repeat the “forgot your password” process for the target account, [email protected] as shown in figure 3. Once they did this, Consultants were able to intercept the PasswordRecovery form request and manipulated the email parameter value with [email protected], which belonged to the target account [email protected]. Figure 4 illustrates this process.
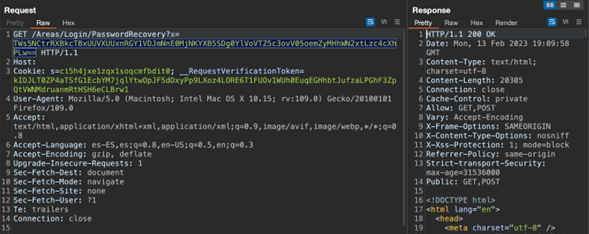
Figure 3 Password Reset Link
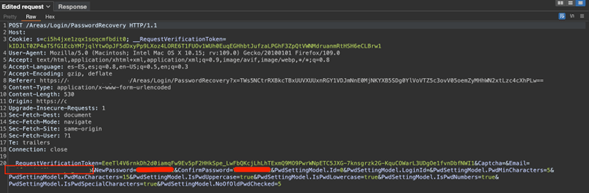
Figure 4 Web Parameter Manipulation
The attacker can now log in into the application as [email protected] user with the new credentials set during the password recovery process, gaining unauthorized access to their account and read potentially sensitive information as shown in figure 5.
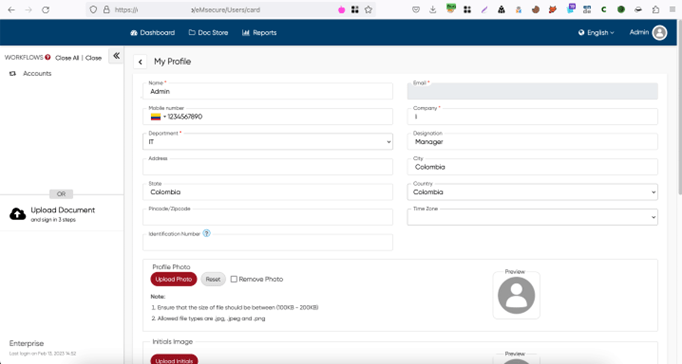
Remediation
An updated version of EMSigner is available at the vendor page.
Credits
The vulnerability was discovered by Jean Paul Granados from SecPro’s Company (https://secpro.co/ – https://secpro.llc/).
References
Vendor page https://www.emsigner.com/
Timeline
2023-02-27
Vulnerability discovered.
2023-05-08
Vendor contacted.
2023-05-24
Vendor replied acknowledging the report.
2023-09-01
Vulnerability patched.
2023-10-27
Public Disclosure.
Contact Us
+1 (804) 256-8316
2034 Eisenhower Ave # 170 Alexandria, VA 22314
Monday-Friday: 9am - 5pm


