Awareness and Human Breach Prevention
Awareness and Human Breach / Leak Prevention
People are the most attacked target in any company;
Do you know if your team is ready to face the next attack and avoid compromising your information due to a simple but catastrophic mistake?.
Well-trained and conscientious people are the strongest link in the chain; We help your business make that bond stronger than ever!
With our great experience we create a curated group of :
-
Games
-
Trainings
-
Conferences
-
Webinars
-
Workshops
-
Exercises
-
Tests
That can clearly and completely reveal all the areas that your company needs to improve, what kind of reinforcement in Cybersecurity awareness your organization needs and the most significant risks you need to address.
Our approach to Awareness Projects can be represented this way:
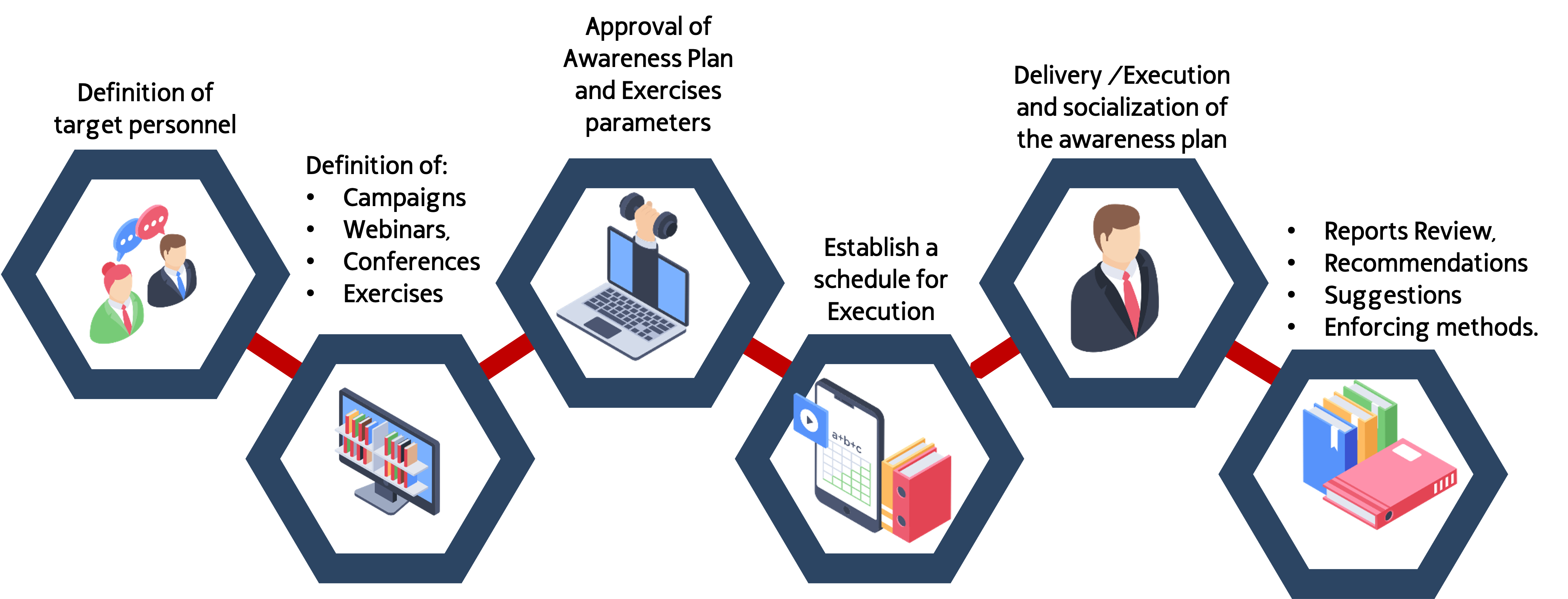
Demonstrative and Disrruptive Talks and Webinars
Our talks are recognized worldwide for 3 specific factors:
-
We demystify cybersecurity as a complex world, reserved for only a handful of people and we bring it to a level understandable for all audiences, regardless of whether they have prior technical knowledge or not, demonstrating that Cybersecurity is everyone’s business.
-
Our Talks are totally demonstrative from a practical aspect, we show the risks and attacks in real time, (We never use pre-recorded videos like everyone else) from the perspective of the attacker, generating a permanent connection with the public, either because of their curiosity or because of the concern of having already fallen into a trap like the ones we demonstrate, generating exactly what we are looking for: awareness
-
We are able to answer any question from the audience and immediately demonstrate how the cybercriminal would act to achieve the objective related to the question we are solving.
Our main Speaker is a worldwide well known expert; he is our CEO: David Pereira; you can access his Speaker One-Sheet David Pereira , or access his SpeakerHub David Pereira Profile.

Hands-On Awareness Workshops and Trainings
Our workshops are totally practical, immersive and oriented to provide the assistant with useful tools and knowledge in the real world that the participant can use immediately.
Taking cybersecurity and the different attack vectors used by adversaries to compromise our information as the core of the workshop, we provide participants with essential knowledge to strengthen the company’s cyber hygiene and reduce existing risk levels.
We empower participants to be aware of the risks, but at the same time able to identify and countermeasure them autonomously, preventing them from being easy victims for a cybercriminals.
Some of the topics of our workshops:
-
Safe Browsing
-
Detection of Malicious Emails
-
Alert Indicators in Social Networks
-
Safe interaction on the internet
-
Many more.

Awareness Gamification and Entertaining
Awareness must be incorporated into the DNA of organizations in the most innovative and memorable ways possible.
For this reason our innovation team permanently implements new ideas to be able to present the information and essential knowledge in the friendliest, simplest and most pleasant way, with the objective of generating an indelible mark in the minds of people in an easy and fluid way.
From interactive guides to game spaces that can be implemented within organizations, along with many more ways to present knowledge about cybersecurity are part of our portfolio.
Contact us for more information about the best way to raise cybersecurity awareness for your Company.

Controlled Social Engineering Campaigns
We all know that people within the organization are the preferred targets of cybercriminals for multiple reasons.
One of the main reasons is for example, high-level technological mechanisms are not required to deceive the victims, it only requires an acceptably credible speech and some technological accessories such as a mail service, or a disposable telephone, among other elements.
For these reasons, Social Engineering is one of the most dangerous attack vectors, since any criminal in the world would be capable of carrying out attacks of this type without spending many resources or having advanced technical knowledge.
Our diagnostic test services offer various alternatives for our clients when they want to check the attitude, prevention and readiness of their work team in the face of a potential attack such as a false email or a false phone call.

Controlled Phishing Campaigns
.Campaigns where we send perfectly composed deceptive mails in a controlled way to the people in the organization defined by the client.
The objective of this exercises is to provide a clear image about how the potential victims inside the organization can react in front of a potentially malicious email and with this scenarios, we can detect various risk factors:
-
Was the fake email opened or not?
-
Was the fake link visited or not?
-
Data was provided by the victim in the fake portal?
-
Was a file attachment downloded by the victim?
-
Was the email forwarded to someone else?
Among other factors, and at the end we deliver a detailed statistical report of the actions carried out by the people involved in the exercise.
With this results the Company can take measures to improve their team awareness like customized trainings or more comprehensive exercises.

Controlled Vishing Campaigns
Campaigns where we make telephone calls in a controlled way to the people in the organization defined by the client with specific pretexts emulating the actions of a nefarious actor trying to convince the potential targets to provide valuable information.
The objective of this exercise is to provide a clear image about how the potential victims inside the organization can react in front of a potentially deceptive phone call.
In this diagnostic, we can detect various factors:
-
Was the call answered?
-
The person accepted our pretext?
-
The person provided some type of data?
-
Did the person provide any private or confidential information of the organization?
-
Did the target follow the Information Disclosure Company Policy or the right procedure in front of an information request?
At the end we deliver a detailed statistical report of the actions carried out by the people involved in the exercise.

Staff Impersonation / Physical Intrusion
Within our tests we can try to access the Company’s facilities pretending to be a client, executive or operator coming from a service provider such as: Communications Company, Internet provider, Construction Company, among others.
The objective is to verify if the company’s physical security measures, protocols and policies are being carried out properly or if, on the contrary, with a uniform, appropriate clothing and a convincing script, a criminal could access the internl facilities of the target company.
At the end we deliver a report of the actions carried out by the people involved in the exercise, the results of the activities and the level of penetration that we managed to obtain together with the attacks and successful techniques used.
For more information about how our services can strengthen your cybersecurity and reduce your attack surface, do not hesitate to contact us.

Contact Us
+1 (804) 256-8316
2034 Eisenhower Ave # 170 Alexandria, VA 22314
Monday-Friday: 9am - 5pm


