Network Security Diagnostics
Network Security Diagnostics
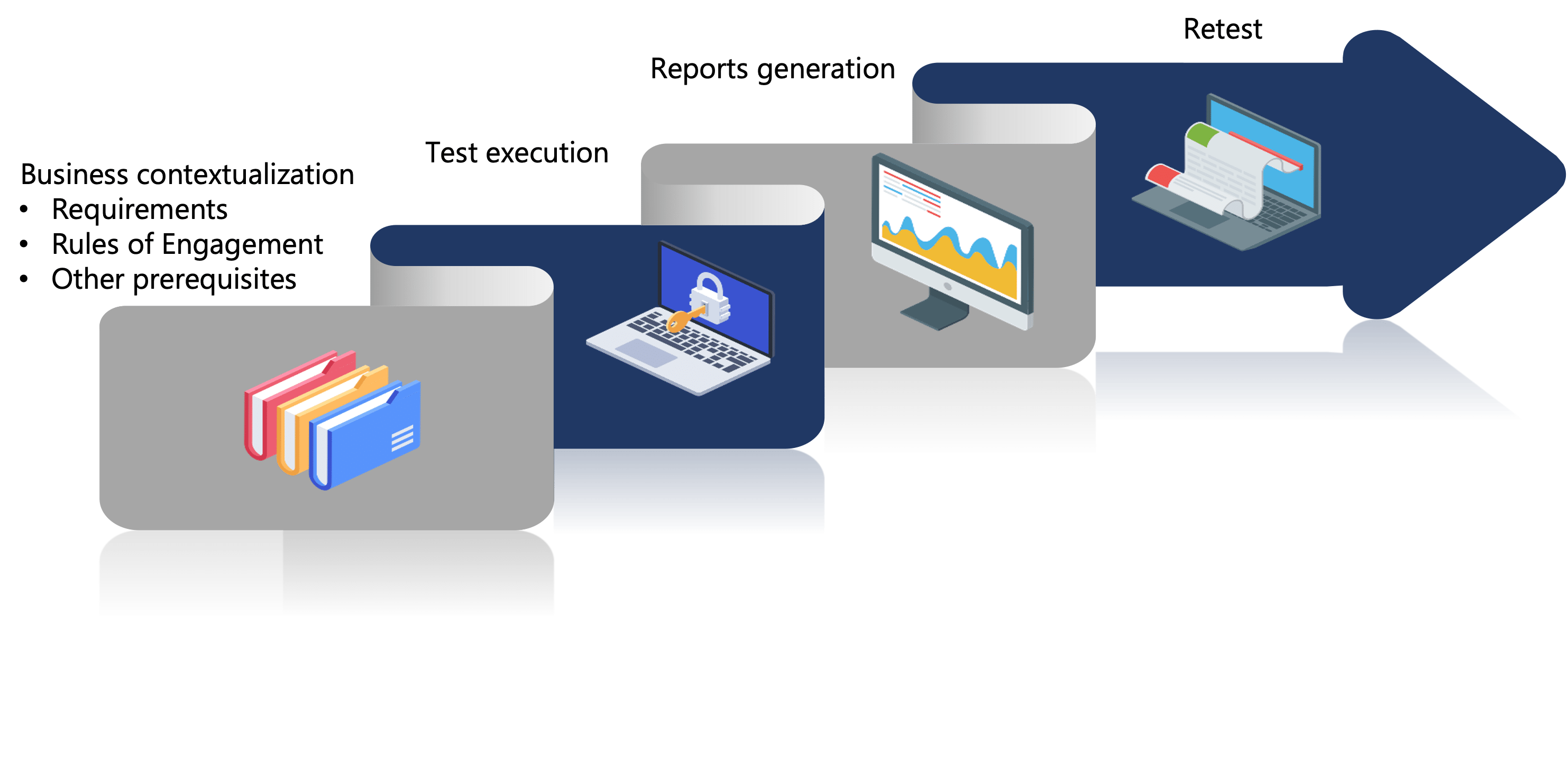
Our Diagnostic Services follows an strict methodology, oriented to provide the most value to our clients; in general each services is composed by:
Internal and External Penetration Testing (Pentesting)
This test aims to find vulnerabilities or security flaws in the systems or the communication devices under evaluation that can be exploited by an adversary or a cyber criminal.
The pentester simulates the execution of tests that a malicious attacker might perform from the following perspectives:
-
Black Box / Cyber criminal Perspective:
-
External attacker without privileges or access to the Devices, Servers, Operating Systems, Applications or Technologies that support the services.
-
-
Grey Box
-
The Attacker have limited Knowledge about the infrastructure; this excercise can include to know the credentials for a low-privilege user account.
-
-
White Box (Audit Perspective)
-
The Attacker posses entire knowledge of the infrastructure, knows the topology, have credentials with full access.
-
Our Pentesting Service follows this stage by stage methodology:

Vulnerability Assessments
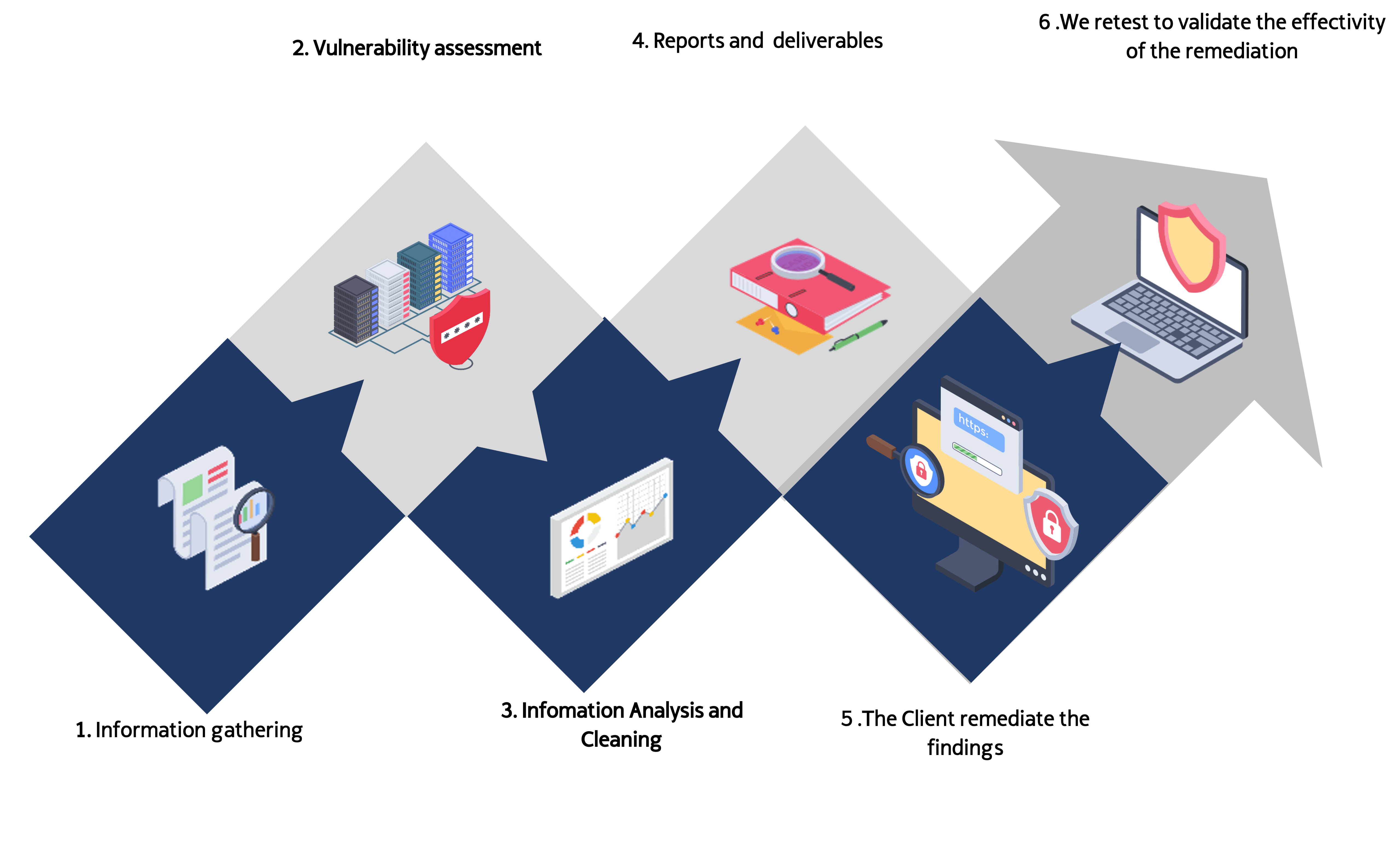
This service consists of the detection and assessment of technical security weaknesses existent in a specific IT infrastructure environment.
This service is executed using market-leading tools for the discovery and analysis of vulnerabilities. Thanks to this service the client organization will be able to:
-
Detect common vulnerabilities.
-
Have visibility of the security status of systems and services.
-
Prioritize action plans and resources for the solution of such vulnerabilities.
-
Evaluate vulnerability mitigation results by comparing with previous scans.
-
Satisfy regulatory compliance requirements (for example: PCI DSS).
In this service, the information received as a result of the automated tools, is deeply analyzed, and all unnecessary or superfluous data that would distort the results of the exercise are filtered out.
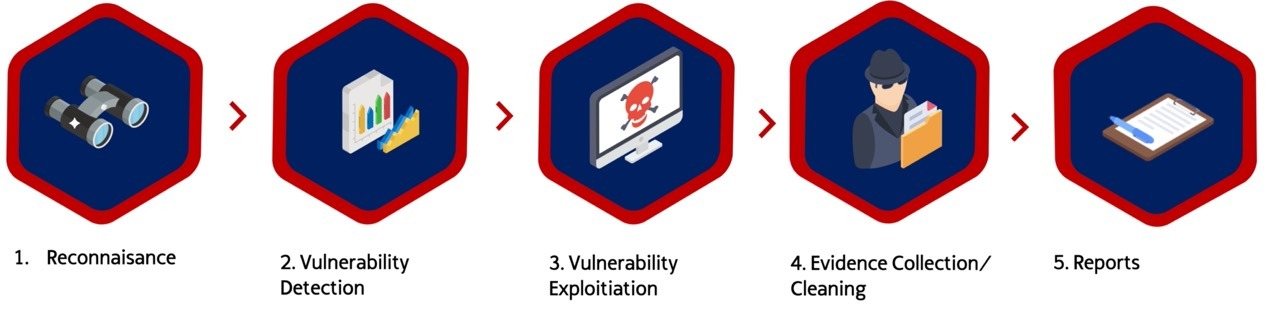
Our Vulnerability Assessment Service follows this stage by stage methodology:

Etical Hacking and Red Team
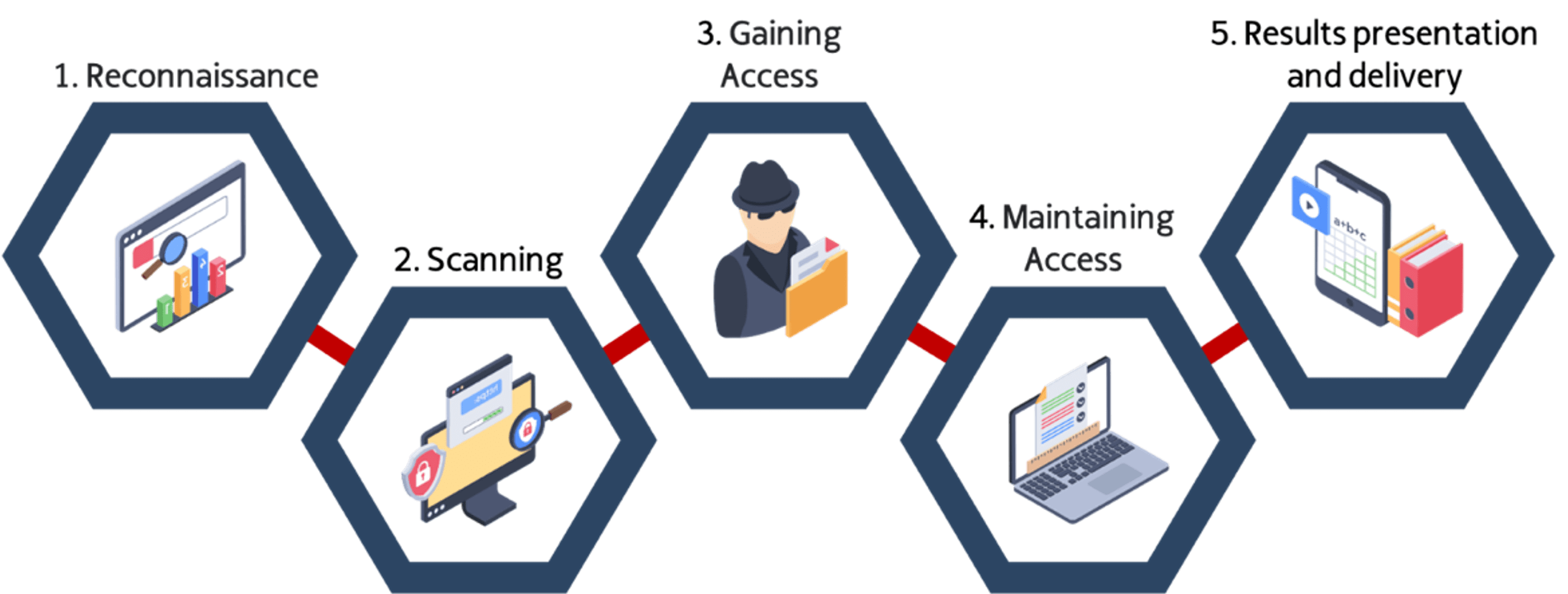
This activity aims to find and exploit security vulnerabilities through unstructured attack activities, following the 5 Stages of the Hacking:
-
Reconnaissance
-
Scanning
-
Gaining Access
-
Maintain Access
-
Cover the Tracks
This means that the experience and knowledge of the expert is used to seek access the platform, infrastructure or facilities in an unauthorized way in the same way that a Cybercriminal (Malicious Hacker) would, using the same tecniques, tools and procedures, but with the autorization and express consent from the owner of the infrastructure.
The service will last as minimum of 15 business days, during which time the different attack activities will be carried out in order to find security gaps.
This activities can include a variety of attacks and social engineering techniques, like:
-
Phishing
-
Vishing
-
Impersonation
-
Tail Gaiting
-
Piggybacking
-
Controlled Malware
-
Physical Intrusion
-
Many more.
Our Ethical Hacking / Red Team service, follows this stage by stage methodology:

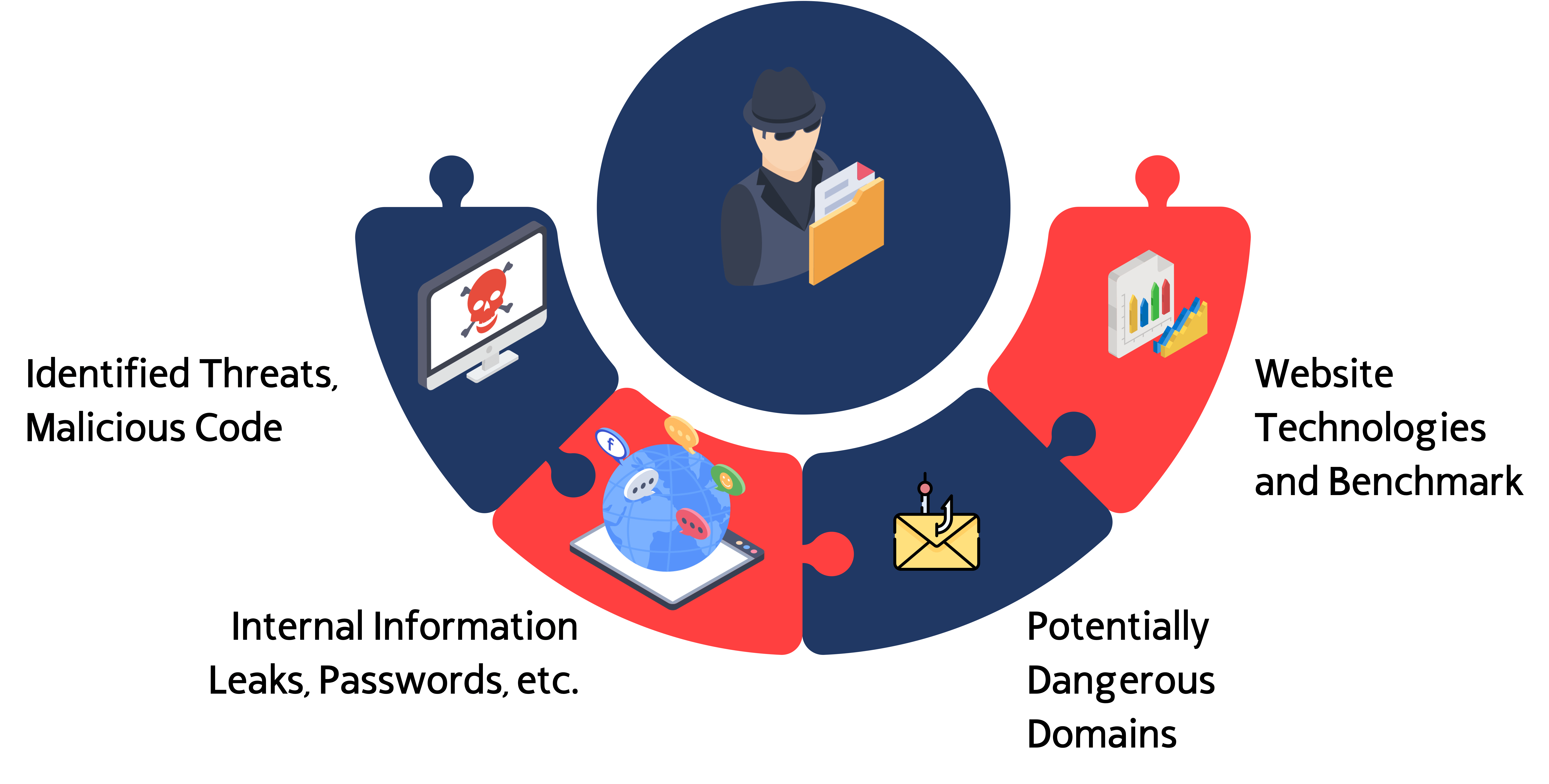
Attack Surface Detection (Internal and External)
Companies sometimes have infrastructure under outsourcing management, or temporal infrastructure that in some moment becomes permanent, or forgotten infrastructure containing private information, with low security or not security at all; and the common factor here is: if a nefarious actor finds this infrastructure, exist a big risk of compromise for the company.
History teach us a lot of cases and examples related with this risks, and how with a simple but effective Attack Surface detection scan that infrastructure can be detected and a disastrous attack can be prevented.
In this service we use Commercial and Proprietary technologies to detect vulnerable surfaces belonging or not to the target comany, and let the company know about the risks involved in each one of the detected assets.
Some of the infrastructure and information that this service can detect:
-
Potentially Dangerous or Fake Domains
-
Exposed Users, Emails
-
Leaked Passwords
-
File Servers
-
Domain Controllers
-
DNS Servers
-
VPN Servers
-
Communication Devices
-
Video Conference Technologies
-
IOT
-
etc.

Contact Us
+1 (804) 256-8316
2034 Eisenhower Ave # 170 Alexandria, VA 22314
Monday-Friday: 9am - 5pm


